Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
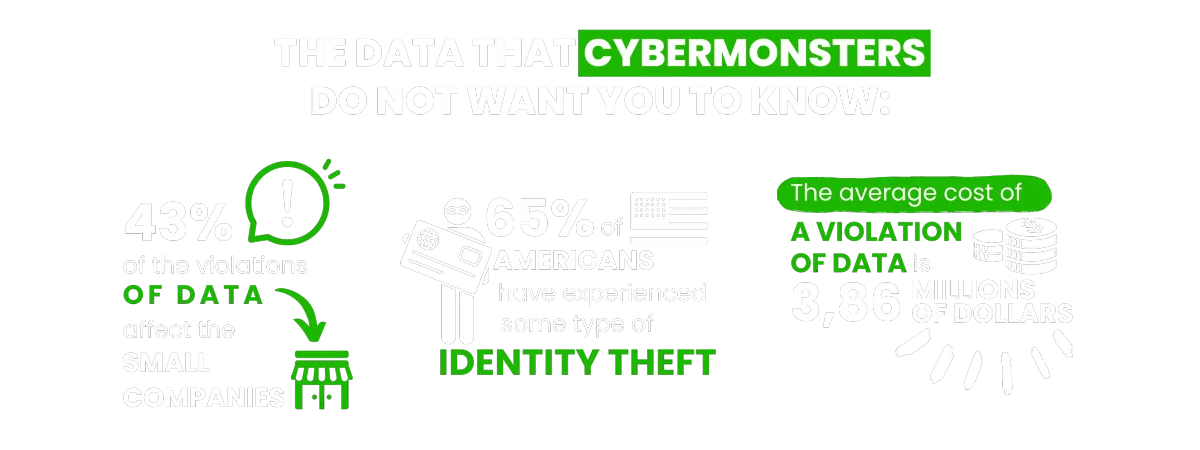
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

The Cybersecurity Alchemist: Transmuting Data Breaches into Golden Opportunities
In the digital age, data breaches have become an unfortunate reality for businesses of all sizes. The immediate aftermath of such incidents is often characterized by panic, financial losses, and a tarnished reputation. However, forward-thinking organizations are increasingly recognizing that these dark clouds can have a silver lining. By adopting the mindset of a cybersecurity alchemist, companies can transform the leaden weight of a data breach into a golden opportunity for growth, innovation, and enhanced security.
1. The Silver Lining of Data Breaches
While it may seem counterintuitive, a data breach can serve as a powerful catalyst for positive change within an organization. The shock of a security incident often shakes companies out of complacency, forcing them to reassess their cybersecurity posture and invest in much-needed improvements. This process of introspection and renovation can lead to a stronger, more resilient business that is better equipped to face the challenges of an increasingly hostile digital landscape.
Moreover, the way a company responds to a breach can significantly impact its long-term reputation and customer relationships. Organizations that demonstrate transparency, accountability, and a commitment to improvement in the wake of a breach often emerge with stronger customer loyalty and a reputation for integrity. This transformation from victim to victor is not just possible; it's becoming increasingly necessary in a world where cybersecurity incidents are viewed as a matter of "when," not "if."
2. Case Study: Company X's Breach Response and Transformation
To illustrate the potential for post-breach alchemy, let's examine the case of Company X, a mid-sized e-commerce platform that experienced a significant data breach in 2019. The incident exposed the personal and financial information of over 100,000 customers, initially resulting in a sharp decline in user trust and a 30% drop in sales.
However, Company X's response to the breach was nothing short of exemplary. Within hours of discovering the incident, they:
Notified affected customers and relevant authorities
Offered free credit monitoring services to all impacted users
Launched a dedicated microsite to provide real-time updates on the breach investigation and remediation efforts
Engaged a top-tier cybersecurity firm to conduct a thorough audit of their systems
In the months following the breach, Company X implemented a series of sweeping changes to its security infrastructure and practices:
Adopted a zero-trust architecture, significantly reducing the potential impact of future breaches
Implemented advanced encryption for all customer data at rest and in transit
Developed a comprehensive employee training program on cybersecurity best practices
Integrated AI-powered threat detection systems to proactively identify and mitigate potential vulnerabilities
The results of these efforts were remarkable. Within a year, Company X had not only regained its pre-breach customer base but had grown it by an additional 15%. Customer surveys indicated a significant increase in trust, with many users citing the company's transparent handling of the breach and subsequent security improvements as key factors in their decision to continue using the platform.

3. Key Strategies for Post-Breach Improvement
Company X's success story provides valuable insights into effective post-breach strategies. Let's delve deeper into some key approaches that can help organizations turn a cybersecurity crisis into an opportunity for growth and improvement.
a) Implementing Advanced Security Measures
A data breach often exposes weaknesses in an organization's existing security infrastructure. This presents an opportunity to implement state-of-the-art security measures that go beyond merely patching the identified vulnerabilities. Advanced strategies might include:
Adopting a zero-trust security model: This approach assumes that no user, device, or network should be trusted by default, even if they are already inside the perimeter. Every access request is thoroughly verified before being granted.
Implementing multi-factor authentication (MFA): MFA adds an extra layer of security by requiring users to provide two or more verification factors to gain access to a resource, significantly reducing the risk of unauthorized access.
Employing data encryption: Robust encryption protocols for data at rest and in transit can render stolen information useless to attackers, minimizing the impact of potential future breaches.
Regular penetration testing: Conducting frequent, comprehensive penetration tests can help identify and address vulnerabilities before they can be exploited by malicious actors.
b) Enhancing Transparency and Communication
One of the most critical aspects of post-breach recovery is how an organization communicates with its stakeholders. Transparency in the aftermath of a security incident can transform a potential PR disaster into an opportunity to demonstrate integrity and commitment to customer security. Effective communication strategies include:
Prompt notification: Inform affected parties as soon as possible, providing clear information about the nature of the breach and its potential impact.
Regular updates: Maintain open lines of communication throughout the investigation and remediation process, keeping stakeholders informed of progress and any new developments.
Clear guidance: Provide affected individuals with actionable steps they can take to protect themselves, such as changing passwords or monitoring their credit reports.
Long-term commitment: Demonstrate an ongoing commitment to security by regularly sharing updates on new security measures and improvements implemented post-breach.
c) Investing in Employee Training
Human error remains one of the leading causes of data breaches. A comprehensive employee training program can significantly reduce this risk while fostering a culture of cybersecurity awareness throughout the organization. Key elements of an effective training program might include:
Regular security awareness training: Conduct frequent sessions to keep employees up-to-date on the latest threats and best practices.
Phishing simulations: Regularly test employees' ability to identify and report phishing attempts through realistic simulations.
Role-specific training: Tailor cybersecurity training to different roles within the organization, ensuring that each employee understands the specific risks associated with their position.
Incident response drills: Conduct regular exercises to ensure all employees know how to recognize and report potential security incidents promptly.
d) Leveraging AI for Threat Detection
Artificial Intelligence (AI) and Machine Learning (ML) technologies are revolutionizing the field of cybersecurity. By leveraging these advanced tools, organizations can significantly enhance their ability to detect and respond to threats in real-time. Some key applications of AI in cybersecurity include:
Anomaly detection: AI algorithms can analyze vast amounts of network traffic data to identify unusual patterns that may indicate a security threat.
Automated threat response: ML-powered systems can automatically initiate predefined response protocols when a threat is detected, significantly reducing response times.
Predictive analysis: AI can analyze historical data and current trends to predict potential future threats, allowing organizations to proactively strengthen their defenses.
User behavior analytics: AI can monitor and analyze user behavior patterns to detect potentially compromised accounts or insider threats.
4. Building Customer Trust Through Proactive Cybersecurity
While recovering from a data breach is crucial, the ultimate goal should be to prevent future incidents and build lasting customer trust. Proactive cybersecurity measures not only protect an organization from threats but also demonstrate a commitment to safeguarding customer data. Some strategies for building trust through proactive cybersecurity include:
Regular security audits and certifications: Undergo frequent third-party security audits and maintain relevant industry certifications (e.g., ISO 27001, SOC 2) to demonstrate a commitment to maintaining high security standards.
Transparent data practices: Clearly communicate how customer data is collected, used, and protected. Provide easy-to-understand privacy policies and give customers control over their data.
Bug bounty programs: Implement a bug bounty program to encourage ethical hackers to identify and report potential vulnerabilities, demonstrating a proactive approach to security.
Customer education: Provide resources and tools to help customers protect their own data and accounts, fostering a sense of shared responsibility for cybersecurity.

5. Conclusion: Turning Vulnerabilities into Strengths
The aftermath of a data breach presents a unique opportunity for organizations to reassess, renovate, and reinvent their approach to cybersecurity. By adopting the mindset of a cybersecurity alchemist, companies can transform the lead of a security incident into the gold of improved practices, enhanced customer trust, and competitive advantage.
The key lies in viewing a breach not as an endpoint, but as a starting point for comprehensive transformation. By implementing advanced security measures, enhancing transparency, investing in employee training, leveraging AI, and building a culture of proactive cybersecurity, organizations can emerge from a breach stronger, more resilient, and better equipped to face the challenges of an increasingly complex digital landscape.
In today's interconnected world, where data breaches have become an unfortunate reality, the ability to turn vulnerabilities into strengths is not just a valuable skill – it's a critical survival trait. The organizations that master this alchemical process will be the ones that thrive in the digital age, earning the trust and loyalty of their customers while staying one step ahead of evolving cyber threats.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



