Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
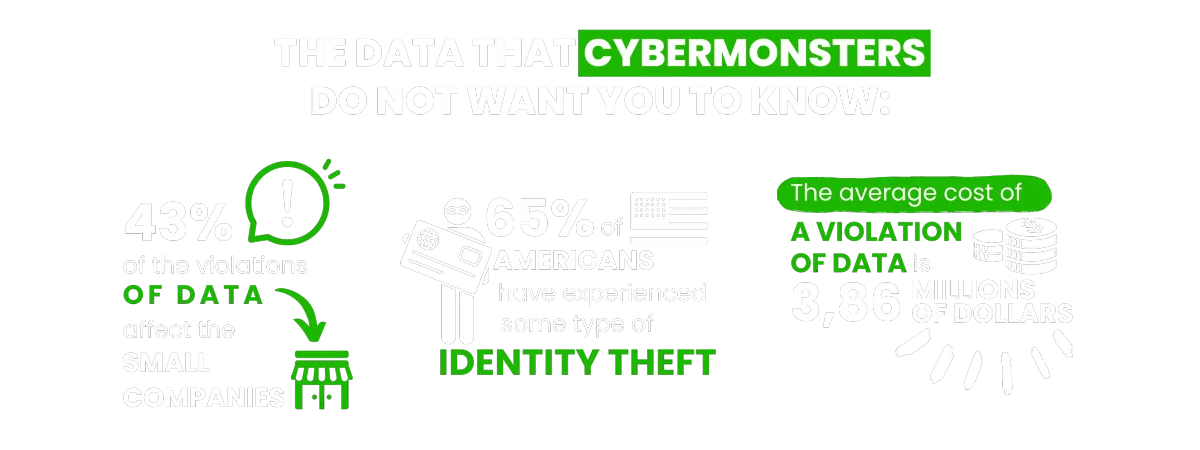
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

Social Engineering Tactics: How to Fortify Your Employees Against Cybersecurity Risks
In an era where digital landscapes are constantly evolving, the human element remains the most vulnerable link in an organization's cybersecurity chain. As Chief Information Security Officers (CISOs), technology professionals, business owners, and entrepreneurs, it's crucial to understand and mitigate the risks posed by social engineering tactics. These sophisticated methods of manipulation can bypass even the most robust technical defenses, making employee awareness and training paramount in safeguarding sensitive information and maintaining the integrity of your digital infrastructure.
Understanding the Threat Landscape
Social engineering is the art of exploiting human psychology to gain access to buildings, systems, or data. Unlike traditional hacking methods that focus on breaching technical defenses, social engineering targets the natural human inclination to trust. Cybercriminals leveraging these tactics often rely on a combination of research, deception, and manipulation to achieve their goals.
The consequences of a successful social engineering attack can be devastating. From data breaches and financial losses to reputational damage and regulatory penalties, the ripple effects can be far-reaching and long-lasting. In 2020 alone, the FBI's Internet Crime Complaint Center reported over $4.2 billion in losses due to cybercrime, with a significant portion attributed to social engineering tactics such as business email compromise (BEC) and phishing scams.
Common Social Engineering Techniques
To effectively protect your organization, it's essential to familiarize yourself with the most prevalent social engineering techniques:
1. Phishing
Phishing remains one of the most common and effective social engineering tactics. Attackers send seemingly legitimate emails or messages that prompt recipients to click on malicious links, download infected attachments, or provide sensitive information. These messages often create a sense of urgency or fear to manipulate victims into acting quickly without proper scrutiny.
Advanced phishing techniques include:
Spear Phishing: Highly targeted attacks that use personalized information to increase credibility.
Whaling: Attacks specifically targeting high-level executives or decision-makers.
Vishing: Voice phishing that uses phone calls to manipulate victims.
Smishing: SMS-based phishing that exploits text messages to deceive users.
2. Pretexting
Pretexting involves creating a fabricated scenario to obtain information or access. Attackers often impersonate authority figures, such as IT support staff, executives, or even law enforcement, to manipulate targets into divulging sensitive data or granting system access. These attacks rely heavily on thorough research and social engineering skills to create convincing narratives that exploit human trust and the desire to be helpful.
3. Baiting
Baiting attacks leverage human curiosity and greed by offering something enticing to lure victims into a trap. This could be in the form of free software downloads, music files, or even physical devices like USB drives left in conspicuous locations. Once the victim takes the bait, malware is installed on their system, or they are redirected to malicious websites that steal their credentials.
4. Tailgating
Also known as "piggybacking," tailgating exploits social norms and politeness to gain unauthorized physical access to secure areas. An attacker might follow an employee through a secure door, pretending to have forgotten their access card or carrying a large box that prevents them from using their own credentials. This technique can be particularly effective in larger organizations where not all employees know each other personally.
5. Quid Pro Quo
In quid pro quo attacks, cybercriminals offer a service or benefit in exchange for information or access. For example, an attacker might pose as IT support, offering to help with a common technical issue in exchange for login credentials. These attacks often target multiple employees within an organization, increasing the chances of finding a willing participant.

Fortifying Your Human Firewall
Given the sophistication and prevalence of social engineering tactics, organizations must adopt a multi-faceted approach to fortify their human firewall. Here are comprehensive strategies to enhance your employees' resilience against these threats:
1. Implement Robust Security Awareness Training
Comprehensive security awareness training is the cornerstone of any effective defense against social engineering. This training should be ongoing, engaging, and tailored to your organization's specific risks and culture.
Key components of an effective training program include:
Regular Phishing Simulations: Conduct periodic phishing tests to assess employee awareness and identify areas for improvement. These simulations should mimic real-world scenarios and evolve to reflect current threat landscapes.
Interactive Workshops: Organize hands-on sessions where employees can practice identifying and responding to various social engineering attempts in a safe environment.
Role-Specific Training: Tailor training content to different departments and job roles, addressing the unique risks and responsibilities associated with each position.
Real-World Case Studies: Share examples of actual social engineering incidents, both from within your industry and beyond, to illustrate the real-world impact of these attacks.
Continuous Learning: Implement a system of microlearning modules, quizzes, and updates to keep security awareness top-of-mind throughout the year.
2. Foster a Culture of Security
Creating a security-conscious culture is crucial for long-term resilience against social engineering attacks. This involves:
Leadership Involvement: Ensure that executives and managers actively participate in and endorse security initiatives, setting an example for the entire organization.
Open Communication: Encourage employees to report suspicious activities without fear of reprimand, creating a supportive environment for security vigilance.
Recognition and Rewards: Implement a system to acknowledge and reward employees who demonstrate good security practices or successfully identify and report potential threats.
Integration into Business Processes: Embed security considerations into everyday workflows and decision-making processes across all departments.
3. Establish Clear Policies and Procedures
Develop and communicate clear, comprehensive policies that address various aspects of information security and social engineering prevention.
These should include:
Data Classification and Handling: Guidelines on how to identify and protect sensitive information.
Access Control: Procedures for granting, reviewing, and revoking access to systems and data.
Incident Response: Step-by-step protocols for reporting and responding to suspected social engineering attempts or security breaches.
Bring Your Own Device (BYOD) Policies: Rules governing the use of personal devices for work-related activities.
Social Media Usage: Guidelines on what information can be shared on social platforms to minimize the risk of information leakage.
4. Leverage Technology Solutions
While the human element is critical, technology plays a vital role in supporting and enhancing your defense against social engineering. Consider implementing:
Multi-Factor Authentication (MFA): Require additional verification steps beyond passwords to access sensitive systems and data.
Email Filtering and Sandboxing: Employ advanced email security solutions that can detect and quarantine suspicious messages and attachments.
Network Segmentation: Limit the potential damage of a breach by segregating critical systems and data from the general network.
Endpoint Detection and Response (EDR): Deploy solutions that can detect and respond to suspicious activities on individual devices.
Security Information and Event Management (SIEM): Implement systems that provide real-time analysis of security alerts generated by applications and network hardware.
5. Conduct Regular Assessments and Audits
The threat landscape is constantly evolving, and so should your defenses. Regular assessments and audits help identify vulnerabilities and areas for improvement:
Penetration Testing: Engage ethical hackers to simulate real-world attacks, including social engineering attempts, to test your organization's resilience.
Security Audits: Regularly review and update security policies, procedures, and controls to ensure they remain effective and aligned with current best practices.
Vulnerability Assessments: Conduct periodic scans of your network and systems to identify potential weaknesses that could be exploited by attackers.
Third-Party Risk Assessments: Evaluate the security posture of vendors and partners who have access to your systems or data.
The Road Ahead: Adapting to Emerging Threats
As technology continues to advance, so do the tactics employed by cybercriminals. Artificial Intelligence (AI) and machine learning are increasingly being used to create more sophisticated and personalized social engineering attacks. Deepfake technology, for instance, poses a significant threat by enabling attackers to create highly convincing audio and video impersonations of trusted figures.
To stay ahead of these evolving threats, organizations must:
Invest in Continuous Research: Stay informed about emerging social engineering techniques and technologies used by attackers.
Collaborate and Share Information: Participate in industry forums and information-sharing networks to learn from peers and contribute to collective defense efforts.
Embrace Adaptive Security: Implement flexible security frameworks that can quickly incorporate new defenses against emerging threats.
Prioritize Privacy: As social engineering often relies on publicly available information, organizations should review their data privacy practices and educate employees on the importance of protecting personal information online.

Conclusion
In the face of increasingly sophisticated social engineering tactics, organizations must recognize that their employees are both their greatest vulnerability and their strongest line of defense. By implementing comprehensive training programs, fostering a security-conscious culture, and leveraging appropriate technological solutions, CISOs, technology professionals, business owners, and entrepreneurs can significantly enhance their organization's resilience against these insidious threats.
Remember, cybersecurity is not a destination but a journey. Continuous improvement, adaptation, and vigilance are key to staying one step ahead of cybercriminals. By investing in your human firewall and creating a holistic approach to security, you can protect your organization's assets, reputation, and future in an increasingly complex digital landscape.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



