Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
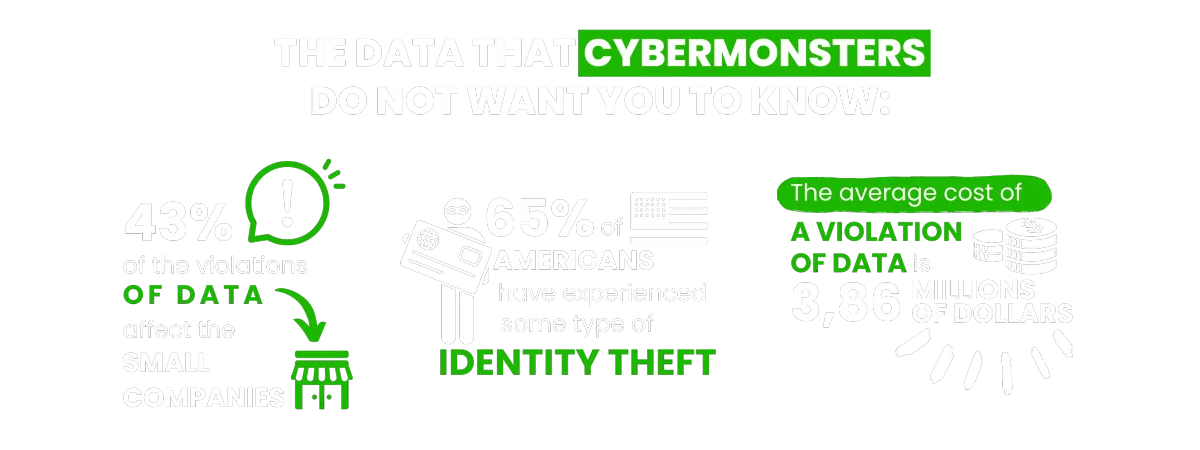
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

The Quantum Leap: How Your Coffee Habits Could Safeguard Your Digital Life
1. Intro: Your morning brew and the quantum brew
Picture this: It's 7 AM, and you're fumbling for your smartphone, eyes barely open, to order your daily caffeine fix through your favorite coffee app. As you tap through your order, little do you know that this mundane morning ritual could soon be at the forefront of a technological revolution. The world of quantum computing is rapidly evolving, and its implications reach far beyond the realm of theoretical physics, potentially reshaping the very fabric of our digital lives – including how we secure our morning coffee runs.
In this exploration of the intersection between quantum computing and everyday cybersecurity, we'll draw surprising parallels between our morning rituals and the future-proofing of our digital defenses. As we journey through the complexities of quantum mechanics and its impact on cybersecurity, we'll discover how the simple act of ordering a latte could become a gateway to understanding – and protecting against – the quantum threat.
2. Quantum computing 101 for the caffeine-powered
Before we dive into the implications for your digital routine, let's take a moment to demystify quantum computing. Much like how a shot of espresso can supercharge your morning, quantum computing has the potential to supercharge computational power beyond our wildest dreams. Traditional computers, which we use daily, process information in bits – binary units that are either 0 or 1. Quantum computers, on the other hand, harness the bizarre properties of quantum mechanics to process information using quantum bits, or qubits.
Qubits can exist in multiple states simultaneously, a phenomenon known as superposition. This property, combined with another quantum quirk called entanglement, allows quantum computers to perform certain calculations exponentially faster than classical computers. It's as if your barista could prepare every possible combination of coffee drinks simultaneously, instantly delivering your perfect brew.
However, this immense power comes with a catch. Just as a perfectly crafted espresso can disrupt your sleep if consumed too late in the day, quantum computers have the potential to disrupt our current cybersecurity landscape. The very algorithms that keep our digital lives secure – from online banking to, yes, coffee-ordering apps – could be rendered obsolete in the face of quantum computing's raw computational might.
3. 'Grounds' for concern: How quantum could crack your latte-ordering app
Now, let's get to the grounds of the matter. The security of your favorite coffee app, like most digital services, relies on encryption. Current encryption methods are based on mathematical problems that are extremely difficult for classical computers to solve. For instance, the widely used RSA encryption relies on the challenge of factoring large numbers – a task that would take today's most powerful supercomputers millions of years to crack.
Enter quantum computers. With their ability to explore multiple solutions simultaneously, they could potentially break these encryption methods in a fraction of the time. Suddenly, the digital equivalent of your coffee shop's loyalty card – along with your credit card information, personal details, and every other piece of data transmitted through the app – could be as exposed as beans without a grinder.
This isn't just about coffee, of course. The same principles apply to online banking, email communication, cloud storage, and virtually every aspect of our digital lives. The advent of large-scale quantum computers could render our current encryption methods as effective as a paper cup against a tsunami of data breaches.

4. Stirring in security: Practical steps to quantum-proof your digital routine
Fear not, digital coffee enthusiasts! Just as baristas have developed techniques to create the perfect crema on your espresso, cybersecurity experts are working tirelessly to develop quantum-resistant encryption methods. These new approaches, collectively known as post-quantum cryptography, aim to create algorithms that are secure against both classical and quantum computers.
While the full implementation of quantum-safe cryptography may still be a few years away, there are steps you can take today to start quantum-proofing your digital routine:
Stay informed: Keep abreast of developments in quantum computing and cybersecurity. Understanding the landscape will help you make informed decisions about your digital security.
Use strong, unique passwords: While not quantum-proof, robust password practices remain crucial. Use a password manager to create and store complex, unique passwords for each of your accounts.
Enable two-factor authentication (2FA): This adds an extra layer of security that remains effective even in a post-quantum world.
Keep software updated: Ensure your devices and apps are always running the latest versions, which often include security enhancements.
Be cautious with sensitive information: Limit the amount of personal data you share online, especially through unsecured channels.
Remember, quantum computers aren't yet advanced enough to break current encryption methods. By adopting these practices now, you're not just protecting against current threats, but also laying the groundwork for a quantum-safe future.
5. The perfect blend: Balancing convenience and quantum-safe practices
As we navigate the transition to a quantum-safe digital landscape, finding the right balance between convenience and security will be crucial. Much like crafting the perfect cup of coffee, it's about finding harmony between different elements.
For instance, the convenience of storing your credit card information in your coffee app for quick morning orders must be weighed against the potential risks in a post-quantum world. You might choose to use a virtual credit card number for such transactions, adding a layer of security without significantly impacting convenience.
Similarly, as quantum-safe encryption methods are developed and implemented, there may be trade-offs in terms of speed or user experience. Just as some coffee enthusiasts willingly sacrifice the convenience of instant coffee for the superior taste of a carefully brewed pour-over, users may need to adapt to new security measures that prioritize long-term safety over short-term convenience.
Companies, too, will play a crucial role in this balancing act. Coffee chains and app developers will need to invest in quantum-safe technologies and clearly communicate the benefits to users. They might offer incentives for adopting new security measures, much like how some cafes offer discounts for using reusable cups.
The key is to start small and build habits over time. Just as you might gradually refine your coffee palate, you can incrementally enhance your digital security practices. Start by auditing your current digital routines, identifying potential vulnerabilities, and implementing quantum-safe practices where possible. Over time, these small changes will compound, creating a robust defense against both current and future threats.

6. Conclusion: Sipping safely in the quantum era
As we stand on the brink of the quantum computing revolution, it's clear that our digital lives – from the most crucial financial transactions to the most mundane morning routines – are set for a significant shake-up. The parallel between our coffee habits and our cybersecurity practices serves as a poignant reminder: just as we've learned to appreciate and perfect the art of brewing coffee, we must now learn to navigate and secure our digital presence in the face of quantum advances.
The quantum future isn't just about threats; it's also brimming with possibilities. Quantum technologies promise to revolutionize fields from medicine to climate modeling, potentially solving some of humanity's most pressing challenges. By embracing quantum-safe practices in our daily digital routines, we're not just protecting our personal information – we're participating in a broader shift towards a more secure and innovative digital future.
So, the next time you reach for your phone to order that morning latte, take a moment to appreciate the complex interplay of technology, security, and everyday life. In the quantum era, every digital interaction, no matter how small, is an opportunity to contribute to a safer online world. Here's to many more secure, quantum-safe coffee runs in the future – may your data be as well-protected as your carefully crafted brew is enjoyed.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



