Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
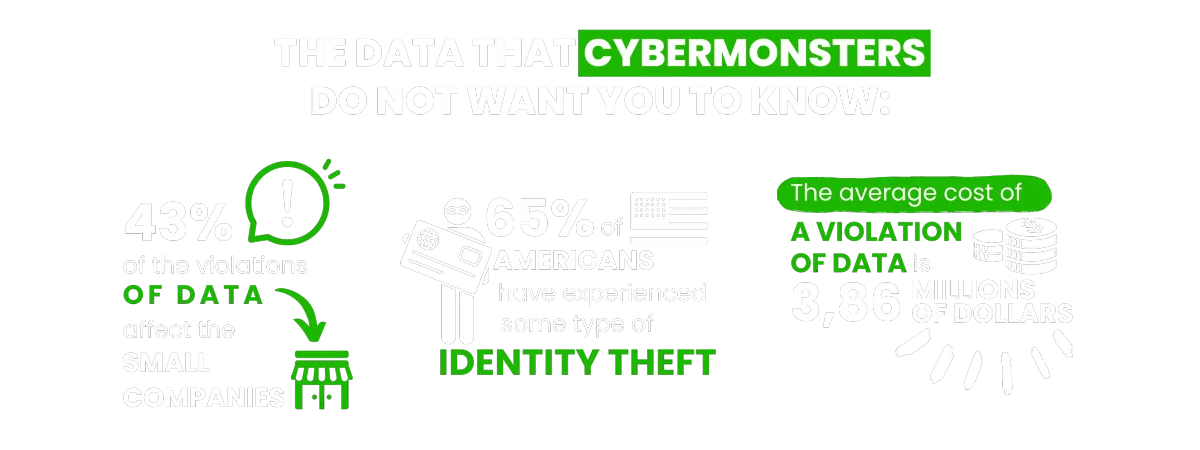
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

Digital Footprints in the Sand: Tracking and Protecting Your Online Trail
In today's digital world, every click, like, and share leaves a mark—a digital footprint that reveals our online activities. As we navigate social media, e-commerce sites, and various online services, we unknowingly scatter pieces of personal information across the internet. This guide explores the nature of digital footprints, their implications, and how to protect your online identity.
1. Introduction to Digital Footprints
Digital footprints are the traces of data we leave behind when we use the internet. These can be as simple as a comment on a blog post or as detailed as our entire search history. Essentially, our digital footprint is a reflection of our online activities, pieced together from various interactions.
With the rise of social media and the increasing digitization of our daily lives, the size of our digital footprints continues to grow. Understanding these footprints is crucial for managing privacy and security in our interconnected world.
2. Types of Digital Footprints: Active vs. Passive
Active Digital Footprints
Active digital footprints are the intentional traces we leave online, such as:
Social media posts and interactions
Blog comments and forum contributions
Online shopping activities
Email communications
Personal websites or blogs
These footprints are easier to manage since they come from our conscious decisions to share information. However, they can also be the most visible and potentially damaging if not carefully curated.
Passive Digital Footprints
Passive digital footprints are the trails we leave behind unknowingly, including:
IP addresses logged by websites we visit
Browsing history tracked by search engines
Location data captured by mobile apps
Metadata from photos and documents we upload
Information collected by third-party cookies
Passive footprints are harder to control since they are created through our normal use of the internet and digital devices. They can reveal a lot about our habits, preferences, and behaviors.
3. Risks Associated with Large Digital Footprints
Having a large digital footprint can pose significant risks:
Identity Theft and Fraud
Cybercriminals can use the information available online to create a comprehensive profile, enabling them to impersonate victims for financial gain. The more information available, the easier it is for them to exploit it.
Reputation Damage
Unmanaged digital footprints can affect personal and professional lives. Old social media posts or controversial comments can resurface years later, damaging reputations and jeopardizing opportunities.
Privacy Breaches
Large digital footprints increase the risk of privacy breaches. More personal information scattered across online platforms means a higher chance of this data being exposed through data breaches or hacks.
Targeted Advertising and Manipulation
Digital footprints can be used for targeted advertising and marketing, which can feel invasive. More concerning is the potential for this information to be used for manipulation, as seen in recent political campaigns.
Physical Security Risks
Oversharing information about travel plans or daily routines can make individuals vulnerable to stalking or burglary.

4. Step-by-Step Guide to Tracking Your Online Presence
Understanding your digital footprint is the first step in managing your online presence. Here’s a guide to help you track and assess your digital trail:
Google Yourself
Search your name with quotation marks for more accurate results. Explore beyond the first page to see what information is readily available about you online.
Check Social Media Platforms
Audit your presence on social media platforms. Log into each and review your privacy settings, posted content, and any information visible to the public.
Use People Search Engines
Use search engines like Pipl, Spokeo, or BeenVerified to see what personal information is available. These services compile information from various public records and online sources.
Set Up Google Alerts
Create Google Alerts for your name and its variations. This will notify you whenever new content mentioning your name appears online.
Review Data Broker Sites
Check data broker websites like Whitepages, Intelius, and MyLife. These sites often compile and sell personal data, and you may need to opt out to remove your information.
Analyze Your Digital Shadows
Consider information that could be linked to you through associations, such as family members’ social media posts or workplace websites.
Examine Your Email Footprint
Use services like Have I Been Pwned to check if your email addresses have been involved in data breaches.
Review Online Forums and Comments
Search for usernames you commonly use on forums and in comment sections. These can often be linked back to your real identity.
Check Image Search Results
Perform an image search of yourself using Google Images or TinEye. This can reveal photos of you that exist online, including those you may not have posted.
Assess Your Professional Online Presence
Review your presence on professional networking sites like LinkedIn, industry-specific forums, and any publications or presentations you’ve been involved with.
5. Strategies to Minimize and Protect Your Digital Footprint
Once you know the extent of your digital footprint, implement strategies to minimize and protect it:
Audit and Clean Up Existing Content
Review all your online accounts and delete or untag yourself from any content that you no longer want associated with your digital identity.
Tighten Privacy Settings
Adjust the privacy settings on all your online accounts to the strictest levels possible. Revisit these settings periodically, as platforms often update their privacy options.
Be Mindful of New Content Creation
Adopt a cautious approach to sharing information online. Before posting anything, consider its potential long-term implications.
Use Strong, Unique Passwords
Implement robust password practices. Use a different, complex password for each account, and consider using a reputable password manager.
Be Wary of Third-Party Apps and Services
Exercise caution when granting permissions to third-party apps and services. Regularly review the list of apps that have access to your accounts.
Limit Personal Information Sharing
Be selective about the personal information you share online. Avoid posting sensitive details like your full birth date or home address on public platforms.
Use VPNs and Private Browsing
Consider using a VPN to encrypt your internet traffic and mask your IP address. Use private browsing modes when accessing sensitive information.
Opt-Out of Data Brokers and People Search Engines
Take the time to opt-out of data broker websites and people search engines that collect and sell your personal information.
Monitor Your Online Presence
Regularly monitor your online presence using the techniques discussed. Set up Google Alerts and respond promptly to any concerning information.
Educate Yourself on Privacy Laws and Rights
Stay informed about privacy laws and regulations, such as GDPR in Europe or CCPA in the United States. Understanding your rights can help you protect your digital privacy.
Consider Digital Estate Planning
Think about the long-term management of your digital presence. Create a digital estate plan that outlines how you want your online accounts and digital assets handled in the event of your incapacitation or death.

6. Tools and Technologies for Managing Online Privacy
A variety of tools and technologies can help manage your online privacy:
Privacy-Focused Web Browsers
Browsers like Brave, Mozilla Firefox, and Tor offer enhanced privacy features.
Virtual Private Networks (VPNs)
VPNs like NordVPN, ExpressVPN, and ProtonVPN encrypt your internet traffic and mask your IP address.
Password Managers
Tools like LastPass, 1Password, and Bitwarden help you generate and store strong, unique passwords.
Ad and Tracker Blockers
Browser extensions such as uBlock Origin, Privacy Badger, and Ghostery block ads and trackers.
Secure Messaging Apps
End-to-end encrypted messaging apps like Signal, WhatsApp, or Telegram ensure that only the intended recipients can read your messages.
Privacy-Focused Search Engines
Search engines like DuckDuckGo and Startpage don’t track your search history.
Email Aliases and Disposable Email Services
Services like SimpleLogin or AnonAddy allow you to create email aliases that forward to your main email address.
Privacy-Focused Analytics Tools
Tools like Plausible or Fathom offer privacy-respecting analytics for website owners.
Digital Footprint Scanners
Tools like Deseat.me and AccountKiller help you identify and delete old online accounts.
Encrypted Cloud Storage
Services like Tresorit, pCloud, and Sync.com offer end-to-end encrypted cloud storage.
Privacy-Focused Operating Systems
Operating systems like Tails or Qubes OS provide heightened security and anonymity.
Data Breach Notification Services
Services like Have I Been Pwned and Firefox Monitor alert you if your email address or passwords appear in known data breaches.
7. Teaching Children About Digital Footprints
Educating children about digital footprints is crucial:
Use Age-Appropriate Language
Tailor your explanations to the child's age and level of understanding. Use simple terms and analogies.
Lead by Example
Model good online behavior and privacy practices. Children are more likely to adopt these habits if they see their parents or guardians prioritizing online safety.
Set Privacy Rules
Establish clear rules for online behavior, such as not sharing personal information, using strong passwords, and being cautious about accepting friend requests from strangers.
Monitor Online Activity
Keep an eye on the child's online activity and be aware of the platforms and apps they use. Regularly review privacy settings.
Discuss Consequences
Explain the potential risks and consequences of oversharing online, such as identity theft, cyberbullying, and reputation damage. Use real-life examples to illustrate these points.
Encourage Open Communication
Create an environment where children feel comfortable discussing their online experiences and any concerns they may have. Address issues promptly and supportively.
Use Educational Tools
Leverage educational resources, games, and apps designed to teach children about digital footprints and online safety.
Regular Check-Ins
Schedule regular check-ins to discuss the child's online behavior and address any new questions or concerns.
By instilling good digital habits early, you can help children develop a healthy and secure approach to their online presence.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



