Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
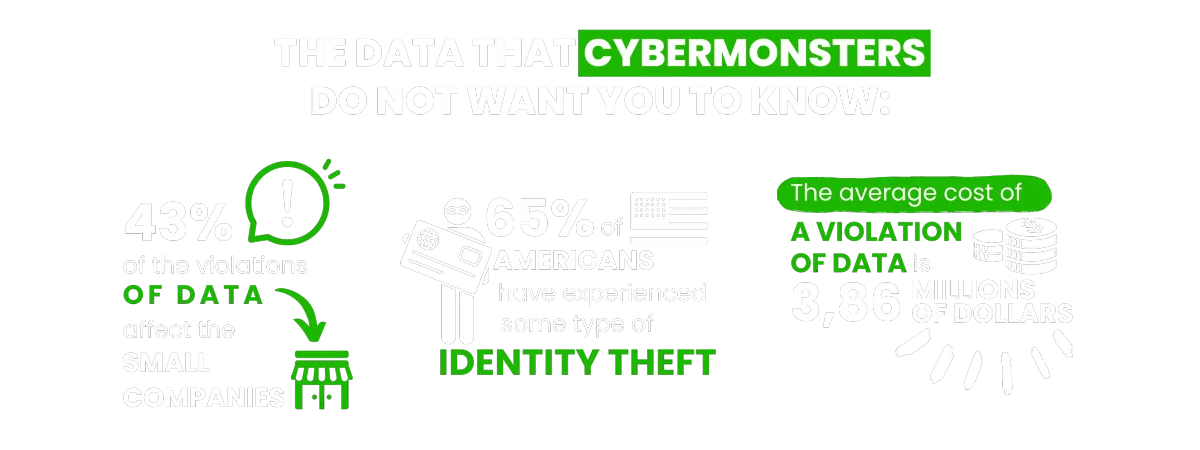
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

Cybersecurity Feng Shui: 7 Ways to Harmonize Your Digital and Physical Spaces
Cybersecurity Feng Shui: 7 Ways to Harmonize Your Digital and Physical Spaces
In a world where our lives are intertwined with technology, it's crucial to seek balance and harmony in both our physical and digital spaces. Introducing Cybersecurity Feng Shui – an approach that blends the ancient Chinese practice of spatial harmony with modern digital safety techniques. This method isn't just about security; it's about creating a peaceful and mindful digital life.
Feng Shui, meaning "wind-water," focuses on harmonizing individuals with their environment through the strategic arrangement of objects. This same philosophy can be applied to our digital spaces to enhance our cybersecurity practices.
As our online presence grows, so does our vulnerability to cyber threats. By integrating Feng Shui principles into our cybersecurity habits, we can create a balanced, secure, and mindful digital existence. Here are seven Feng Shui-inspired cybersecurity practices to harmonize your digital and physical spaces, promoting safety and peace of mind.
Clear Your Digital Clutter
Clutter obstructs the flow of positive energy, both in Feng Shui and in your digital life. Digital clutter can hinder productivity and increase your exposure to cyber threats. Start by organizing your digital files, deleting unnecessary documents, and unsubscribing from irrelevant email lists. This creates a serene digital space and reduces the amount of personal information accessible to cybercriminals.
Example: Imagine you're a busy mom juggling work and family life. You sit down to manage your household budget, but your desktop is a mess of files, and your inbox is overflowing with unread emails. It's overwhelming! By spending just 15 minutes each week organizing your files and unsubscribing from unwanted emails, you'll not only feel more in control but also reduce the risk of missing important emails or exposing sensitive information.
Implement a digital filing system that mirrors your physical document organization. Use descriptive file names and logical folder structures. Regularly review and delete old files, especially those with sensitive information. By maintaining a clutter-free digital environment, you enhance efficiency and minimize the risk of data breaches.
Review and clean up your social media presence. Remove old posts with personal information, update privacy settings, and be mindful of what you share online. In the digital world, less often means more security.
Create Strong 'Walls' (Firewalls and Passwords)
In Feng Shui, walls and doors protect and control energy flow. In the digital realm, firewalls and passwords serve this purpose. They are your first defense against unauthorized access and potential threats.
Ensure robust firewalls are enabled on your devices. Regularly update firewall settings to protect against new threats. Think of passwords as the locks on your digital doors. Create strong, unique passwords for each account using a mix of uppercase and lowercase letters, numbers, and special characters. Use a reputable password manager to generate and securely store complex passwords.
Story: I once met a business owner named Kathy who thought her small business wouldn’t be targeted by cybercriminals. She used simple passwords for convenience. One day, she found her accounts hacked, and sensitive customer information was compromised. After this incident, Kathy realized the importance of strong passwords and multi-factor authentication. Now, she uses a password manager and has educated her employees about the importance of digital security.
Implement multi-factor authentication (MFA) wherever possible. MFA adds an extra layer of security by requiring multiple verification methods to access an account. It's like adding a security system to your digital locks, making it significantly harder for unauthorized access.

Promote Good 'Energy Flow' (Update Software Regularly)
Good energy flow is essential for harmony in Feng Shui. In cybersecurity, this translates to keeping your software and systems up-to-date. Regular updates improve functionality and patch security vulnerabilities, ensuring a smooth and secure digital experience.
Set up automatic updates for operating systems, applications, and security software. Cyberattacks often exploit known vulnerabilities in outdated software. Staying current with updates closes potential entry points for malicious actors.
Example: Think of software updates as cleaning out the cobwebs from your home. Just as you wouldn’t leave dust to accumulate in your living space, don’t let your software become outdated and vulnerable. I remember a time when my friend Alex ignored his phone's update notifications. One day, his phone was infected with malware that accessed his banking app, causing a financial headache. Regular updates could have prevented this!
Update not just your computers and smartphones but also other connected devices like smart home systems, routers, and IoT devices. These can be weak points in your digital security if left unattended.
Regularly review and update apps on your devices. Uninstall those you no longer use, as they may continue accessing your data or contain unpatched vulnerabilities. Maintaining a lean, up-to-date digital environment promotes good energy flow and enhances your overall cybersecurity posture.
Balance Yin and Yang (Offline and Online Security Measures)
Feng Shui emphasizes balance, often represented by yin and yang. In cybersecurity, balance your online security measures with offline practices.
While robust online security tools are essential, don’t neglect physical security measures. Use privacy screens on devices in public spaces to prevent visual hacking. Avoid leaving devices unattended, even in seemingly safe environments like workplaces or coffee shops.
Use a combination of cloud storage and local backups for important data. Cloud storage offers convenience and protection against physical damage or theft, while local backups give you control over your data and access without an internet connection.
Story: I once met a corporate leader, Morgan, who always ensured her team followed strict online security protocols. However, one day she left her laptop unattended in a coffee shop, and it was stolen. Important company data was at risk. This incident taught Morgan the importance of balancing online and offline security measures.
Implement a 'clean desk' policy at home and work. Don’t leave sensitive documents or sticky notes with passwords visible. Securely store or shred documents containing personal information when no longer needed.
Balancing digital security with physical safeguards creates a comprehensive approach to protecting your information, embodying the yin and yang of cybersecurity.
Use 'Protective Symbols' (Antivirus and VPNs)
In Feng Shui, symbols and objects offer protection and ward off negative energy. In the digital realm, antivirus software and Virtual Private Networks (VPNs) are our protective symbols.
Invest in a reputable antivirus program and ensure it's always active and up-to-date. Modern antivirus software protects against a wide range of threats, including malware, spyware, and ransomware. Some offer additional features like safe browsing extensions and password managers.
A VPN acts as a protective shield for online activities, especially when using public Wi-Fi networks. It encrypts internet traffic, making it harder for cybercriminals to intercept data. Choose a trusted VPN provider with a no-logs policy and strong encryption standards.
Example: I remember my cousin, who traveled frequently for work, often used public Wi-Fi without a VPN. One day, while at an airport, his personal information was intercepted and used for fraudulent activities. After this incident, he began using a VPN for all his online activities, significantly enhancing his online privacy and security.
Use ad-blockers and anti-tracking extensions in web browsers. These tools protect your privacy by blocking intrusive ads and preventing websites from tracking online behavior.
Like Feng Shui symbols, these digital protections work best when used consistently and with other security practices.
Mindful Placement of Devices
Feng Shui values the placement of objects within a space. Apply this principle to how you position and use digital devices.
Place your router in a central location, away from windows and external walls, to optimize signal strength and reduce network access from outside your home.
Be mindful of where you use devices, especially with sensitive information. Avoid accessing confidential data in public spaces. At home, set up your workspace to minimize screen visibility from windows or doorways.
Example: Think of your home office. If you position your desk facing a window where passersby can see your screen, you’re risking visual hacking. By simply repositioning your desk, you can protect sensitive information from prying eyes.
Think about the placement of smart home devices, especially those with cameras or microphones. Position them to respect privacy for you and your family.
Create a 'device-free' zone in your home, like the bedroom or dining area. This promotes better sleep and family interaction and reduces the risk of exposing sensitive information during non-work hours.
By being intentional about where and how you use devices, you create a more secure and harmonious digital environment.
Regular 'Cleansing Rituals' (Data Backups and Security Audits)
Feng Shui includes regular cleansing rituals to clear negative energy and promote renewal. In the digital world, adopt similar practices through regular data backups and security audits.
Implement a consistent backup strategy for important data. Use a combination of cloud storage, external hard drives, and network-attached storage (NAS) devices. Regular backups protect against data loss due to hardware failure or cyberattacks and provide peace of mind.
Conduct periodic security audits of your digital environment. Review account settings, check for unfamiliar logins or activities, and update privacy settings across platforms. Use this time to change passwords, especially for critical accounts.
Story: My friend Sarah always felt overwhelmed by the amount of digital data she had. One day, her computer crashed, and she lost important files because she hadn’t backed them up. After this incident, she started performing regular data backups and security audits, giving her peace of mind knowing her data was safe.
Regularly review app permissions and revoke access for those you no longer use or trust. This minimizes your digital footprint and reduces the risk of data exposure through third-party breaches.
Use privacy-focused tools to scan devices for malware and assess your overall security posture. Many cybersecurity companies offer free tools to identify potential vulnerabilities in your digital setup.
Incorporating these cleansing rituals into your routine maintains a healthy and secure digital environment, much like regular Feng Shui practices maintain positive energy in a physical space.

Conclusion: Achieving Digital Peace of Mind Through Balance
As we navigate an increasingly digital world, Feng Shui principles offer a unique and holistic approach to cybersecurity. Applying these ancient concepts to our modern digital lives creates a balanced, secure, and mindful online experience.
Remember, like Feng Shui, cybersecurity is an ongoing practice. It requires regular attention, adjustment, and mindfulness. By clearing digital clutter, creating strong defenses, promoting good energy flow through updates, balancing online and offline security measures, using protective tools, being mindful of device placement, and performing regular cleansing rituals, you can achieve a harmonious balance between your physical and digital spaces.
As you implement these Cybersecurity Feng Shui practices, you'll find that they not only enhance digital security but also contribute to a sense of calm and control in your overall life. In a world where digital stress and anxiety are common, this balanced approach to cybersecurity can be a powerful tool for achieving peace of mind.
Embrace the art of Cybersecurity Feng Shui and transform your digital life into a secure, balanced, and harmonious space. After all, in both the physical and digital worlds, true security comes from creating an environment of mindfulness, balance, and positive energy flow.
Stay safe and live happily ever cyber!
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



