Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
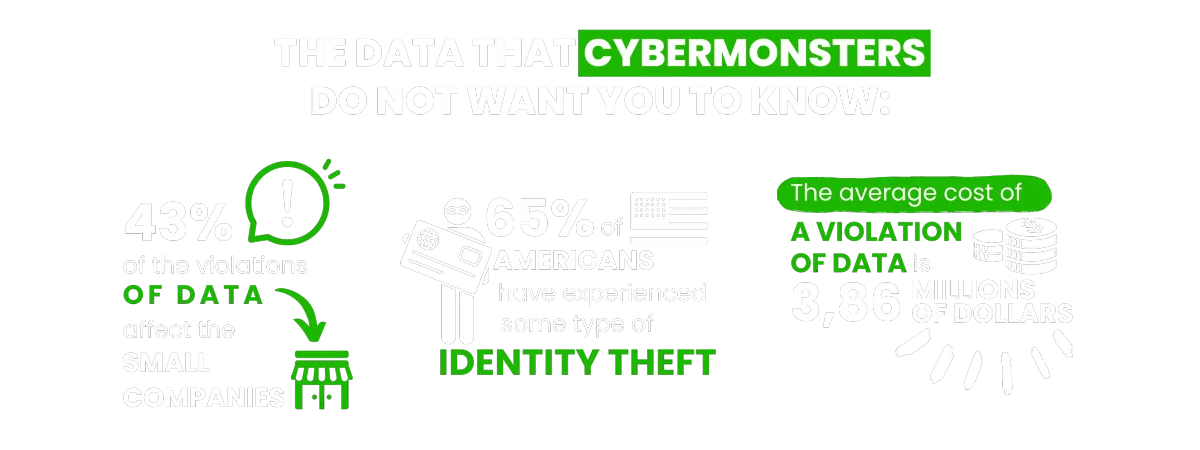
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

AI on the Dark Side: Outsmarting the Next Wave of Cyber Threats
AI on the Dark Side: Outsmarting the Next Wave of Cyber Threats
Imagine this: You're scrolling through your inbox when you see an email from your bank. It looks legitimate, maybe even urgent. They need you to update your account information immediately. Without a second thought, you click the link and enter your details.
But here's the twist: that email wasn't from your bank. It was from a cybercriminal using AI to craft a convincing phishing scam. And just like that, your personal information is compromised.
Unfortunately, this is not just a hypothetical scenario. AI is rapidly changing the face of cybercrime, making scams more sophisticated and harder to detect. But don't worry, knowledge is your best defense. In this blog post, we'll explore how bad actors are using AI, reveal the warning signs of these new threats, and equip you with the tools you need to stay safe.
Together, we'll embrace the "Be I AM" principle—being Intentional, Aware, and Mindful—to outsmart these cyber tricksters and keep our digital lives secure.
Decoding the New Threats
AI isn't just a helpful assistant anymore – it's become a powerful tool in the arsenal of cybercriminals. Let's take a look at how these digital troublemakers are using AI to up their game:
Supercharged Phishing: Remember that fake email from your "bank"? AI can make those scams even more convincing. It can analyze your language patterns and create emails that sound just like you, making them harder to spot.
Malware Makeovers: AI can create new versions of malicious software (malware) faster than you can say "antivirus." These ever-changing viruses are designed to evade traditional security tools, making them a serious threat.
Social Media Imposters: Ever seen a fake profile on social media that looked a little too real? That's probably AI's handiwork. These convincing bots can spread misinformation, steal personal data, and even manipulate public opinion.
And these are just a few examples. Cybercriminals are constantly finding new ways to exploit AI, making the threat landscape more complex than ever before. It's like playing a game of digital cat and mouse, where the rules are constantly changing.
For someone like Kathy, who's already overwhelmed by technology, this can feel like a nightmare. And for Morgan, the cybersecurity professional, the stakes are even higher, as she's responsible for protecting her entire organization. But don't lose hope! Understanding the threat is the first step towards protecting yourself.
Think of it like this: Would you go for a hike in the woods without knowing what kind of wild animals might be lurking? Probably not. The same principle applies to the digital world. By learning to identify the warning signs of AI-powered attacks, you'll be better equipped to navigate the cyber jungle safely.
The Evolution of Cyber Attacks
Remember the days when a hacker was a lone wolf, hunched over a computer in a dark basement? Those days are long gone. Thanks to AI, cyber attacks are evolving faster than ever before, becoming more widespread, sophisticated, and difficult to detect.
Think of it like this: if traditional cybercrime was like a small, manageable campfire, AI-powered attacks are like a raging wildfire, spreading rapidly and leaving a trail of destruction in their wake.
Here's a glimpse into how AI is changing the game:
Speed and Scale: AI can automate tasks that used to take humans hours or days to complete. This means cybercriminals can launch attacks on a massive scale, targeting thousands of victims simultaneously.
Adaptive Learning: AI can learn from its mistakes and improve over time. This means cyberattacks are becoming more sophisticated and harder to defend against with each iteration.
The Weaponization of Data: AI can analyze vast amounts of data to identify vulnerabilities and tailor attacks to specific individuals or organizations. This makes attacks more personal and more effective.
These advancements pose serious challenges for individuals and families, who may feel like they're constantly playing catch-up with the latest threats. And for cybersecurity professionals like you and me, the pressure is on to keep pace with this rapidly evolving landscape and protect their organizations from increasingly complex attacks.
It's easy to feel overwhelmed, even a bit scared. I know I was when I fell victim to identity theft. It felt like my entire life had been turned upside down, and I didn't know where to turn for help. But that experience also taught me the importance of being prepared and staying informed. After all, the only way to outsmart a cybercriminal is to understand how they operate.
Now, let's move on to the good news: we're not powerless in the face of these new threats. By embracing the "Be I AM" approach, we can arm ourselves with the knowledge and skills needed to navigate this evolving digital landscape.
Ready to discover your AI defense strategy? Let's continue diving in!
Your AI Defense Strategy: The Be I AM Approach
Navigating the digital world is like walking through a bustling city. There are wonders to behold, but also dangers lurking around every corner. The "Be I AM" approach is your personal GPS, guiding you safely through the AI-powered cyber jungle.
Here's how to put it into action:
Be Intentional: Before you use an AI tool or service, ask yourself: Why am I using this? What data is it collecting? How will it be used? By understanding the potential risks and benefits, you can make informed decisions about how to incorporate AI into your life.
Be Aware: Pay attention to the warning signs of AI-powered attacks. Does that email from your "bank" look a little off? Are you getting friend requests from people you don't know? Trust your gut and double-check anything that seems suspicious.
Be Mindful: Don't just click on links or download attachments without thinking. Take a moment to pause, breathe, and consider the potential consequences. This simple act of mindfulness can save you a lot of trouble down the road.

It's important to remember that AI is a tool, not a magic bullet. No single solution can protect you from every threat. But by adopting a "Be I AM" mindset, you'll be well on your way to staying safe and secure in the digital age.
In addition to the "Be I AM" mindset, let's add another powerful tool to your AI defense kit: the secret family or business safe word.
Think of it as a verbal two-factor authentication for your real life. It's a simple, yet effective way to protect yourself from AI-powered scams like deepfakes, where bad actors can convincingly mimic someone's voice or image.
Here's how it works:
Choose a word or phrase: Pick something that's easy for your family or team to remember but not easily guessable by others. It could be a favorite inside joke, a reference to a shared memory, or even a nonsensical word.
Keep it offline: Don't share your safe word on social media or anywhere else it could be discovered by cybercriminals.
Use it to verify requests: If you receive a call or message asking for money, sensitive information, or access to an account, ask the caller to provide the safe word. If they can't, you know it's not the real person.
This simple step can add an extra layer of security to your personal and professional life, helping you stay one step ahead of the bad guys.
Here's how this strategy can benefit both at a personal and business level:
Personal: As an individual, mother, parent, guardian and businesswoman, you can use a safe word with your family and colleagues to ensure that any urgent requests are legitimate. This can give you peace of mind knowing that your loved ones and your business are protected from AI-powered scams like deepfakes.
Professionals: As a cybersecurity leader, professional or aspiring tech student, you can implement a safe word policy within your organization or school. This can help prevent social engineering attacks where employees, students, and individuals are tricked into divulging sensitive information or authorizing fraudulent transactions.
Remember, the best defense is a good offense. By being proactive and implementing simple strategies like the safe word, you can significantly reduce your risk of falling victim to AI-powered scams.
Here are some additional tips to boost your AI defense:
Keep your software updated: Cybercriminals often exploit vulnerabilities in outdated software. By keeping your apps and operating systems up-to-date, you'll make it harder for them to gain access to your devices.
Use strong passwords: Avoid using the same password for multiple accounts. Choose strong, unique passwords that are difficult to guess. Consider using a password manager to keep track of them all.
Be cautious about sharing personal information: Think twice before sharing sensitive data online, especially on social media. Remember, cybercriminals can use this information to impersonate you or target you with personalized attacks.

Conclusion:
The rise of AI-powered cyber threats may seem daunting, but don't despair. By embracing the "Be I AM" approach and adding a secret safe word to your arsenal, you can outsmart the Cybermonsters and protect yourself, your family, and your business.
Remember, knowledge is your most powerful weapon. Stay informed, stay vigilant, and most importantly, stay safe in the ever-evolving digital jungle.
Let's all commit to living Happily Ever Cyber!
Call to action:
Share this blog with your friends and family to help them stay safe.
Sign up for our newsletter to receive the latest cybersecurity tips and insights.
Join our community in social media @Way2protect. Our focus is to learn how to protect what matters most and enjoy the online world with peace and grace.
What other AI-powered threats worry you? Share your thoughts in the comments below!
FAQs: AI on the Dark Side
What is AI being used for in cyber attacks?
AI is used to automate and enhance phishing scams, create more sophisticated malware, impersonate people on social media, and even generate fake audio or video (deepfakes).
How can I tell if an email or message is an AI-powered scam?
Look for unusual requests, generic greetings, grammar errors, or suspicious links. If it feels off, trust your instincts and verify the request through another channel.
Is my personal information safe in an AI-powered world?
While AI can enhance security in many ways, it also poses new risks to privacy. It's crucial to understand how your data is being collected and used and to be mindful of what you share online.
What can I do to protect myself from AI-powered cyber threats?
Follow the "Be I AM" approach: Be Intentional, Aware, and Mindful of your online activities. Use strong passwords, keep software updated, and be cautious about sharing personal information.
Should I be scared of AI?
While AI-powered threats are a reality, fear is not the answer. By staying informed and taking proactive steps to protect yourself, you can confidently navigate the digital world.
Can AI be used to fight cybercrime?
Absolutely! AI is also being used to detect and prevent cyberattacks. It can analyze vast amounts of data to identify patterns and anomalies that could indicate malicious activity.
How can I teach my kids about the risks and benefits of AI?
Start by explaining AI in simple terms, using examples they can relate to. Discuss both the positive (like helpful tools and apps) and negative (like potential scams) aspects of AI. Encourage critical thinking and responsible online behavior.
What should I do if I think I've been a victim of an AI-powered scam?
Immediately report the incident to the relevant authorities (e.g., your bank, the police) and take steps to secure your accounts and devices.
Are businesses doing enough to protect themselves from AI cyber threats?
While many businesses are investing in AI-powered security solutions, there's always more that can be done. It's important for organizations to stay up-to-date on the latest threats and adopt a multi-layered approach to cybersecurity.
What does the future hold for AI and cybersecurity?
AI will continue to play a significant role in both cyber attacks and defenses. It's crucial to stay informed and adapt our security practices to meet the evolving threat landscape.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



