Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
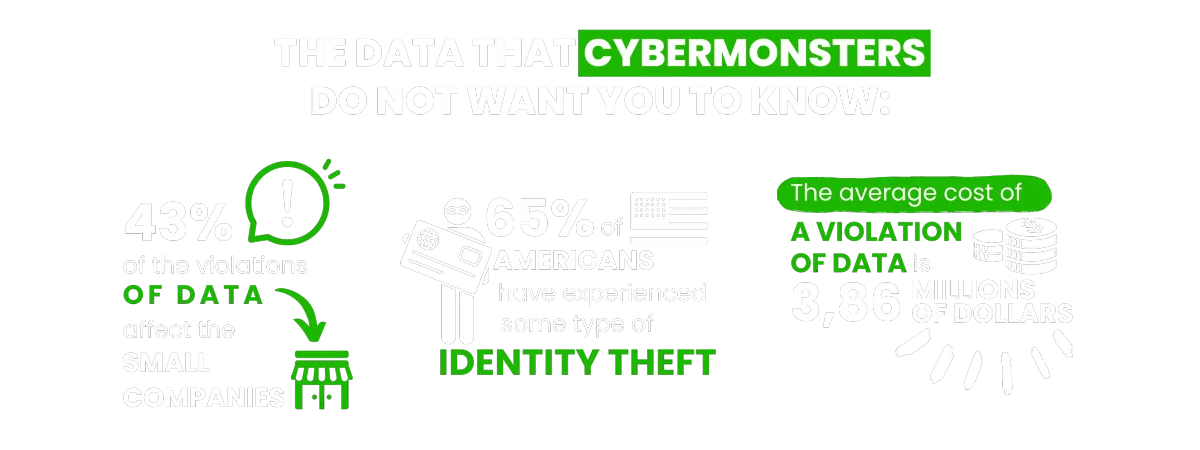
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

AI-Powered Scams: How to Protect Your Business
Cybersecurity leaders understand the persistent threat of phishing attacks, social engineering, and other scams targeting businesses. Now, with the rise of artificial intelligence (AI), scammers have an even more powerful tool in their arsenal. AI makes their attacks more believable, personalized, and harder than ever to detect.
AI: The New Weapon in a Scammer's Toolkit
Let's imagine a few alarming scenarios, made more realistic by the power of AI:
The Fake CEO Email That Cost Millions: It's a Friday afternoon, and your finance manager receives an email that seemingly comes directly from the CEO. The language is familiar, slightly urgent, requesting a wire transfer to a new vendor to secure a "time-sensitive" deal. Acting swiftly, they initiate the transfer, unaware that they've just fallen victim to a devastating AI-powered CEO impersonation scam.
This year the news reported a real case where fraudsters used a convincing deep fake video call to impersonate the CEO, instructing a finance executive to wire $25 million in a seemingly urgent situation. This demonstrates the power of AI in bypassing human safeguards.
Targeted Vendor Fraud – "Just an Invoice Update": Your accounts payable team receives an email that looks like it's from one of your regular suppliers. It mentions a change in bank details and politely asks for future payments to be routed to a new account. Busy and trusting, someone updates the information, only to later discover the real vendor never sent this notice.
Attackers often use AI to generate thousands of phishing emails, mimicking employee writing styles and referencing internal projects. Recent trends involve requests for gift cards, seemingly innocent, but designed to quickly siphon off funds.
I was attending an event with female entrepreneurs and the person sitting next to me had exactly this type of fraud one hour prior to our meeting. She was devastated and didn’t realize the magnitude of the phishing email’s scams until it happened to her company.
Ransomware 2.0 – Your Data Held Hostage, and They Know What to Target: Instead of a generic attack, an AI-powered ransomware variant infiltrates your network. It silently scans your files and systems, identifying not just any data, but the most crucial client records, project files, and backups. The ransom demand is astronomical, calculated to cause maximum pain.
In other words, Ransomware as a Service (RaaS) with AI elevates the extortion, the ransomware gangs offer easy-to-use AI-enabled tools that identify your most valuable data. They demand higher ransoms for critical assets, crippling businesses even if some backups are intact.
The Disgruntled Customer That Never Was: Negative reviews and a sudden social media backlash erode trust in your company. Oddly, no real customer seems to be behind the complaints. Then you realize – AI-powered bots are spreading disinformation, tarnishing your hard-earned reputation with fake attacks.
The Long Con: When Your Chatbot is the Spy: AI-powered chatbots deployed on compromised websites or social media platforms pose as customer support. They subtly gather personal data from users, piece by piece, or even lure them into downloading malware under false pretenses.

Beyond Headlines: Lessons for Leaders
These cases aren't just sensational. Ask yourself:
Does It Have to Be "Perfect"? Scammers play on our emotions and rush us. A deepfake doesn't have to be flawless for someone to fall for it in the heat of the moment. What safeguards do you have against urgent, unusual requests?
Are You Thinking in Volume? Traditional security often focused on the big attack. Yet, smaller, persistent scams add up or pave the way for bigger breaches. Is your security monitoring granular enough?
What is Your Largest Attack Surface? The supply chain and employees are prime targets for AI-powered social engineering. Are you scrutinizing your partners' security, and fostering a culture of cyber vigilance within your team?
Could You Be the Next Target? It's easy to dismiss attacks against other companies as their fault. But AI tools are scalable. What would a highly personalized attack exploiting your company's public data look like?
Beyond the Sensational: How AI Powers These Scams
These stories may feel exaggerated, but the underlying tactics are shockingly real. Here's how AI is being weaponized:
Deepfakes: AI can generate realistic fake videos or audio, making it seem like your CEO is authorizing a fraudulent request or a trusted supplier is changing their payment details as the example we just viewed above.
NLP for Personalized Attacks: Natural Language Processing (NLP) allows AI to analyze public information about your company and employees. This lets scammers craft phishing emails that sound authentic or mimic a vendor's usual communication style.
Automated Network Mapping: AI-powered tools can probe your networks for vulnerabilities, pinpointing the most critical servers to encrypt in a ransomware attack.
Adapting Your Defense: Proactive Strategies
Staying ahead of these evolving threats requires a multi-layered approach, including these crucial elements:
AI-powered Threat Detection: Invest in solutions that analyze network traffic, user behavior, and even language patterns, spotting subtle anomalies that humans might miss. AI can be a powerful defense against AI-powered attacks.
Continuous Employee Training: AI-powered phishing simulations that evolve in difficulty are vital. Regularly train your team to spot fake emails or websites, no matter how well crafted. Emphasize verification processes and reporting unusual requests, even from "trusted" sources.
At Way2Protect®, we believe in the power of collaboration and innovation when it comes to cybersecurity education. That's why we've partnered with Hacker Rangers, a leading gamification platform for cybersecurity training, to bring our unique approach to mindfulness and storytelling to their immersive learning environment. Through this partnership, we offer to help elevate your cybersecurity training:
Mindfulness and Storytelling: We reinforce cybersecurity concepts with guided meditations for focus and resilience, along with interactive stories that highlight the impact of breaches, creating a more engaging and impactful experience.
Customization: We work with you to incorporate real-world case studies or align the training with your company's specific policies and procedures, ensuring the training directly addresses your unique risks.
Measurable Results: By combining the power of gamification, mindfulness, and storytelling, our partnership offers a truly revolutionary approach to cybersecurity education – one that doesn't just teach skills but also transforms attitudes and behaviors. Track learner progress and adapt the training over time for maximum effectiveness.
Zero-Trust Architecture: Implement strict access controls, multi-factor authentication, and network segmentation. Assume that any user or device could be a potential entry point and limit lateral movement within your systems.
Staying Informed: The AI threat landscape changes rapidly. Follow reliable cybersecurity resources in social media like our channels at Way2Protect for updates, and adapt your defenses accordingly.

Building a Cyber-Smart Culture: It Starts with People
Empower employees to become your first cybersecurity defense line:
Be Aware: Encourage reporting of suspicious activity. A culture of transparency reduces the risk of scams escalating.
Be Intentional: Foster mindfulness about the data shared online and when interacting with external parties. Question anything out of the ordinary, even if it seems persuasive.
Be Mindful: Teach employees to pause before clicking links, opening attachments, or responding to urgent requests. A moment of critical thinking could make all the difference.
Remember, if you're ready to take your cybersecurity training to the next level and Manage the Human Risks of your organization, we invite you to experience the Way2Protect difference within the Hacker Rangers platform. Contact us today to learn more about how we can help you create a customized training program that empowers your team to be Cyber-Self Defenders. Together, we can create a culture of cybersecurity awareness, resilience, and mindfulness that will keep your organization safe and secure in the digital age.
Call To Action: Is your business ready for AI-driven threats? Let’s connect in social media @Way2Protect and visit us at https://sandraestok.com
FAQ’s Your AI Cybersecurity Questions Answered
1. I've heard about deepfakes. Could someone really impersonate my CEO with AI?
* Unfortunately, yes. AI-generated deepfakes are becoming alarmingly realistic. Protect yourself by having strict verification processes in place for any unusual financial requests or changes to sensitive data, even if they seem to come from someone you trust.
2. Can AI really make phishing attacks more convincing?
* Absolutely. AI can analyze your company's public information, employee communication styles, and even mimic vendor patterns for highly personalized attacks. That's why scrutinizing every email, no matter how legitimate it appears, is crucial.
3. My company isn't that big. Do I really need to worry about AI attacks?
* Yes! AI tools are readily available to cybercriminals. Any business can be a target, and your smaller size might make you seem like a softer target. Don't fall victim to complacency – proactive AI-focused defenses are essential.
4. What can AI do beyond phishing and impersonation?
* AI has wide-ranging applications in cybercrime. It can map your networks for vulnerabilities, assist in ransomware attacks, and even automate interactions to gather valuable intel for future targeting. Stay informed about evolving AI threats.
5. How can I train my employees to spot AI-powered scams?
* Regular training with realistic AI-generated phishing simulations is key. Partner with cybersecurity training platforms that emphasize mindfulness and real-world scenarios, offering a holistic approach to staying vigilant.
6. Our IT department handles security. Isn't that enough?
* IT is your first line of defense, but your employees are your last. A human-centric approach is vital. Empower your team with the knowledge and mindset to be skeptical and report suspicious activity.
7. Where can I find reliable information about AI cyber threats?
* Reputable sources like Way2Protect® and industry cybersecurity organizations offer regular updates and insights on this evolving threat landscape. Stay informed to stay ahead of attacks.
8. Investing in AI-specific security seems expensive.
* Think of security as a long-term investment rather than a cost. The financial and reputational damage of a successful AI-powered breach far outweighs the cost of prevention and training.
9. Is there anything I can do to protect my supply chain from AI attacks?
* Yes! Include cybersecurity standards in your vendor contracts, and even consider offering assistance for smaller suppliers to meet your requirements.A single breach can undermine your entire defense.
10. I'm worried, but where do I start?
* Knowledge is the first step! Seek expert assessments to identify your vulnerabilities and prioritize defenses. Companies like Way2Protect® offer guidance to build a robust cybersecurity strategy against AI-powered threats cultivating a Cyber-Self Defense approach.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



