Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
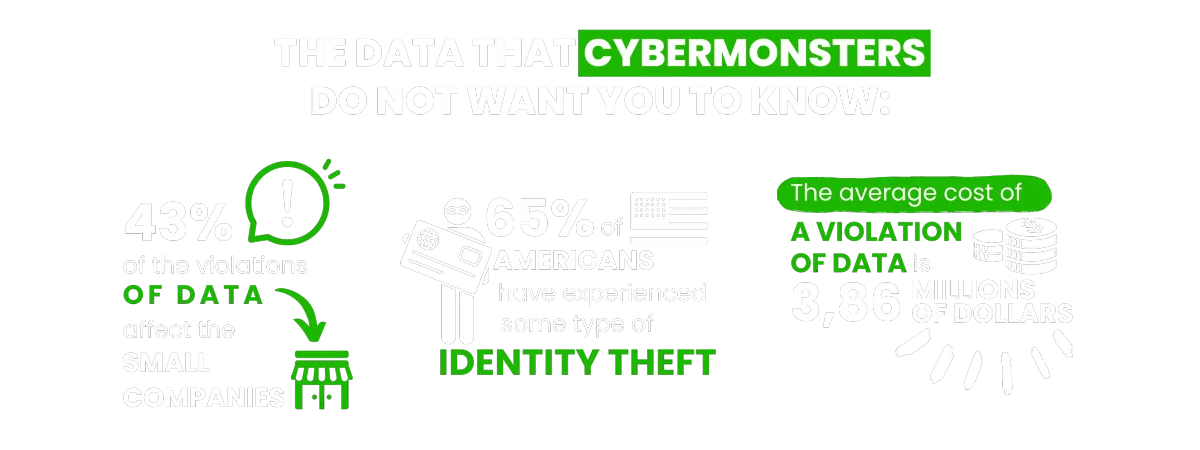
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

AI Cybersecurity: Unmasking the Risks, Maximizing the Rewards – A Practical Guide for Businesses
Picture this: You're sitting in your office, sipping your morning coffee, when your phone buzzes with a news alert. A major company just fell victim to a cyberattack, costing them millions and exposing sensitive customer data. Your heart skips a beat. Could your business be next?
Now, imagine a different scenario. Your cybersecurity team is alerted to a potential threat by an AI-powered system, long before any damage is done. The system quickly analyzes the situation, recommends a course of action, and your team swiftly neutralizes the threat. You breathe a sigh of relief, knowing your business is protected.
Which scenario do you prefer?
The truth is, both are possible in today's world. Artificial Intelligence (AI) is rapidly transforming the cybersecurity landscape, offering both incredible promise and potential peril. It's a double-edged sword, capable of both defending against and perpetrating cyberattacks.
But don't worry, this isn't a doom-and-gloom story.
In this practical guide, we'll unmask the risks of AI in cybersecurity and show you how to maximize its rewards. We'll explore how AI is revolutionizing the way businesses protect themselves, offer actionable steps to implement AI effectively, and share real-world examples of companies using AI to stay ahead of the curve.
Think of it as your roadmap to navigating the exciting, sometimes daunting, world of AI cybersecurity.
By the end of this guide, you'll be equipped with the knowledge and tools to make informed decisions about how to leverage AI to safeguard your business, while staying mindful of its potential risks. Because in the digital age, cybersecurity isn't just about technology – it's about being intentional, aware, and mindful in every interaction with the online world.
So, let's dive in and explore how AI can become your company's most powerful ally in the fight against cybercrime.
The Promise of AI in Cybersecurity: Your Digital Superhero?
So, what exactly makes AI such a game-changer in cybersecurity? Imagine AI as your digital superhero, equipped with superhuman abilities that can keep your business safe from the ever-evolving threats lurking in the digital world. Here's how AI is transforming the cybersecurity landscape:
1. Threat Detection and Response: The AI Watchdog
Remember those old-school burglar alarms that would blare if someone tripped a sensor? AI is like that, but on steroids. It constantly monitors your systems, networks, and data for any signs of unusual activity. And unlike a traditional alarm, AI can actually analyze the situation and determine if it's a real threat or a false alarm. If it spots something suspicious, it can alert your cybersecurity team, or even take immediate action to contain the threat, like blocking a malicious IP address or isolating an infected device.
2. Data Analysis and Pattern Recognition: The AI Detective
Imagine sifting through mountains of data, looking for a single needle – that's what cybersecurity professionals often have to do. AI is like a super-powered detective, able to quickly analyze massive amounts of data and spot patterns that humans might miss. This helps identify vulnerabilities in your systems before attackers can exploit them, predict potential attack vectors, and even uncover hidden relationships between seemingly unrelated events.
3. Automation of Routine Tasks: The AI Assistant
Tired of repetitive tasks? AI feels the same way. It can automate many of the mundane but essential tasks that keep your business secure. This includes things like patching software vulnerabilities, triaging security incidents, and even generating reports. By freeing up your cybersecurity team from these tasks, AI allows them to focus on more strategic initiatives, like threat hunting and incident response planning.
Benefits for Businesses: Superpowers for Your Bottom Line
The superpowers of AI translate into some serious benefits for your business:
Increased Efficiency and Accuracy: AI can analyze data and detect threats much faster and more accurately than humans, leading to quicker response times and reduced risk of errors.
Proactive Defense: By predicting and identifying threats early on, AI can help you stop attacks before they happen, saving you time, money, and headaches.
Reduced Workload: Automating routine tasks frees up your cybersecurity team to focus on more complex and strategic issues, making them more effective and efficient.
Improved Decision-Making: AI-powered analytics can provide valuable insights into your security posture, helping you make data-driven decisions about resource allocation and risk mitigation.
In a nutshell, AI is like having a tireless, ever-vigilant guardian watching over your digital assets. It's not just about protecting your business from cyberattacks; it's about empowering you to make smarter decisions and stay ahead of the curve.
But before you start imagining a world where AI solves all your cybersecurity problems, it's important to remember that there's another side to this story. AI isn't just a force for good – it can also be used for nefarious purposes.
In the next section, we'll delve into the darker side of AI in cybersecurity and explore the risks you need to be aware of. Stay tuned!

The Pitfall of AI in Cybersecurity: When Your Superhero Turns Supervillain
While AI can be a powerful ally in the fight against cybercrime, it's important to remember that it's a tool, not a magic bullet. And like any tool, it can be misused. In the wrong hands, AI can become a formidable weapon for cybercriminals, creating new and evolving threats that businesses need to be prepared for.
1. AI-Powered Cyberattacks: The Rise of the Machines
Imagine a hacker using AI to create highly sophisticated phishing emails that are virtually indistinguishable from legitimate ones. Or a malware that constantly evolves and adapts to evade traditional security measures. These are just a few examples of how AI can be weaponized to launch more effective and harder-to-detect cyberattacks.
2. Deepfakes and Disinformation Campaigns: The War on Truth
Deepfakes, or AI-generated videos and audio that are nearly impossible to distinguish from the real thing, can be used to spread misinformation, manipulate public opinion, and even damage reputations. Imagine a deepfake video of your CEO making a controversial statement, or a fake news article that goes viral and causes your company's stock to plummet. The potential for harm is immense.
3. Synthetic Identity Theft and Fraud: The Identity Crisis
AI can also be used to create synthetic identities, which are fabricated personas that combine real and fake information. These synthetic identities can be used to open fraudulent accounts, apply for loans, and even commit crimes, making it harder for businesses to verify the identity of their customers and partners.
4. Ethical Concerns and Biases in AI Algorithms: The Unintended Consequences
AI systems are only as good as the data they are trained on. If that data is biased, the AI system will be too. This can lead to discriminatory outcomes, such as denying loans to certain groups of people or flagging certain individuals as security risks. It's crucial for businesses to carefully consider the ethical implications of using AI and to ensure that their systems are fair and unbiased.
Navigating the AI Cybersecurity Landscape: Staying Ahead of the Game
The evolving nature of AI-powered threats can be overwhelming, but it's not all doom and gloom. By understanding the risks and taking proactive steps to mitigate them, you can harness the power of AI while minimizing the potential pitfalls.
In the next section, we'll provide you with a practical guide on how to navigate the AI cybersecurity maze, including tips on assessing your needs, choosing the right tools, and developing a comprehensive strategy. Stay tuned to learn how you can protect your business in the age of AI.

A Practical Guide for Businesses: Navigating the AI Cybersecurity Maze
Feeling a bit overwhelmed? Don't worry, you're not alone. The rapid advancement of AI in cybersecurity can feel like navigating a complex maze. Many executives and non-technical folks are asking the same questions you might be pondering:
"Isn't AI just hype? What real benefits can it bring to my business?" We'll address this by showcasing the tangible ways AI enhances security, from quicker threat detection to automating tedious tasks.
"I'm not a tech expert. How can I understand which AI tools are right for my company?" We'll provide a simple breakdown of different AI tools and their functions, along with tips for choosing the right fit for your specific needs and budget.
"Could AI actually make my company less secure?" This is a valid concern. We'll delve into the risks of AI, like the potential for malicious use, and offer guidance on how to mitigate those risks.
With the right guidance and tools, you can find your way to a safer and more secure future for your business. Here's your step-by-step playbook:
Step 1: Self-Reflection: Assess Your Needs and Readiness
Before diving headfirst into AI, take a step back and assess your organization's specific cybersecurity needs and readiness for AI implementation. Ask yourself these questions:
What are our biggest cybersecurity challenges and pain points?
Do we have the necessary data infrastructure and resources to support AI tools?
Are our employees comfortable with and knowledgeable about AI?
What are our ethical boundaries and concerns regarding the use of AI?
"How much will all this cost? Is AI cybersecurity only for big corporations?" Not at all! We'll discuss how AI solutions can be scaled to fit different budgets and company sizes.
Answering these questions will help you identify the areas where AI can have the most impact and determine if your organization is ready to embrace this powerful technology.
Step 2: Choose Your Tools Wisely: Finding the Right Fit for Your Business
The world of AI cybersecurity tools can feel like a crowded marketplace, but it doesn't have to be overwhelming. The key is to focus on your specific needs and budget.
How much will all this cost? Is AI cybersecurity only for big corporations? Not at all! AI solutions come in all shapes and sizes, with options available for every budget. Think of it like choosing the right car: you wouldn't buy a sports car for hauling cargo, and you wouldn't buy a pickup truck for zipping around town. The same goes for AI tools. There are enterprise-level solutions with all the bells and whistles, as well as more streamlined, affordable options perfect for smaller businesses.
Here are a few categories to consider:
Threat Intelligence Platforms: These platforms use AI to collect and analyze threat data from various sources, helping you identify and respond to emerging threats more quickly.
Vulnerability Scanners: AI-powered scanners can automatically detect vulnerabilities in your systems and applications, allowing you to patch them before they can be exploited.
User and Entity Behavior Analytics (UEBA): UEBA tools use AI to establish baselines of normal user and system behavior, making it easier to spot anomalies that could indicate a security breach.
Deception Technology: This involves deploying decoys and traps to lure attackers away from your real systems and gather intelligence about their tactics.
Security Orchestration, Automation, and Response (SOAR): SOAR platforms use AI to automate incident response workflows, improving efficiency and reducing response times.
When choosing tools, consider factors like ease of use, scalability, integration with your existing systems, and of course, cost. Don't be afraid to ask for demos or trials before making a decision.
How do I know if a vendor's AI solution is truly effective?
Don't be shy about asking the right questions:
What specific problems does your AI tool solve?
How does your AI model learn and improve over time?
Can you provide case studies or references from other businesses?
What kind of training and support do you offer?
What metrics do you use to measure the effectiveness of your solution?
Look for vendors who are transparent about their technology, have a proven track record, and are willing to invest in your success. Remember, the goal is to find a partner, not just a product.
Remember, the most effective AI cybersecurity solution isn't necessarily the most expensive or complex one. It's the one that best aligns with your specific needs and empowers you to make informed decisions about your company's security.
some real-world AI cybersecurity tools and vendors, categorized by company size:
Large Enterprises
CrowdStrike:Their Falcon platform leverages AI for endpoint protection, threat intelligence, and incident response. https://www.crowdstrike.com/falcon-platform/artificial-intelligence-and-machine-learning/
Darktrace:This company specializes in AI-powered network security, using unsupervised machine learning to detect anomalies and threats. https://darktrace.com/
Vectra AI:Offers AI-driven network detection and response (NDR) solutions to identify hidden threats and automate security operations. https://brainit.com/products/vectra
IBM Security QRadar Advisor with Watson:This tool uses cognitive AI to analyze security data and provide actionable insights for threat hunting and incident response. https://securityintelligence.com/ibm-qradar-advisor-with-watson-revolutionizing-the-way-security-analysts-work/
TrustedSec AI - TrustedSec's Impede Detection Platform is designed to revolutionize detection engineering. https://impede.ai/
Medium-Sized Businesses
SentinelOne:Their Singularity platform provides AI-powered endpoint protection and response, combining prevention, detection, and automated remediation. https://www.sentinelone.com/platform/
Vectra AI: Vectra AI is an AI-driven threat detection and response platform that uses machine learning to identify and prioritize cyber threats in real-time. It is suitable for medium-sized businesses with limited security resources. https://www.vectra.ai/
Fortinet FortiAI: Fortinet FortiAI is an AI-powered security solution that uses machine learning and deep neural networks to detect and prevent cyber threats across networks, endpoints, and cloud environments. https://www.fortinet.com/products/fortiai
Sophos Intercept X: Sophos Intercept X is an AI-powered endpoint protection solution that uses deep learning to detect and block known and unknown malware, ransomware, and other cyber threats. https://www.sophos.com/en-us/products/endpoint-antivirus
Tessian:This company specializes in AI-powered email security, preventing data loss and phishing attacks by analyzing email content and user behavior. https://www.tessian.com/
Small Businesses
Avanan Email Security: Avanan is an AI-powered email security solution that safeguards email systems from phishing, malware, and other email-based threats. It uses AI and machine learning to detect and block threats. https://www.avanan.com/true-ai
Check Point Harmony Endpoint: Check Point Harmony Endpoint is an AI-powered endpoint security solution that protects devices from malware, ransomware, and other cyber threats. It uses AI and machine learning algorithms to detect and block threats in real-time. https://www.checkpoint.com/harmony/endpoint/
Check Point CloudGuard: Check Point CloudGuard is an AI-powered cloud security solution that helps secure cloud infrastructure and applications. It uses AI and automation to detect and block threats. https://www.checkpoint.com/cloudguard/
Sophos Intercept X:This endpoint protection solution uses AI to detect and block malware, exploits, and ransomware attacks.https://ai.sophos.com/
Malwarebytes:Offers AI-powered anti-malware and endpoint protection solutions designed to protect against a wide range of cyber threats including malware.ai. https://www.malwarebytes.com/blog/detections/malware-ai
SlashNext:Provides real-time phishing protection for email, mobile, and web applications using AI to identify and block sophisticated phishing attacks. https://slashnext.com/
These are just a few examples, and the best tool for your business will depend on your specific needs and budget. It's always recommended to do thorough research and compare different vendors before making a decision.

Step 3: Develop Your AI Cybersecurity Strategy: The Roadmap to Success
Having the right tools is just the first step. To truly harness the power of AI in cybersecurity, you need a comprehensive strategy. This should include:
Clearly defined goals and objectives: What do you want to achieve with AI in cybersecurity?
Ethical guidelines: How will you ensure that your use of AI is fair, transparent, and respects privacy?
Training and education: How will you ensure that your employees understand and can effectively use AI tools?
Data management: How will you collect, store, and analyze data to train and improve your AI systems?
Incident response plan: How will you incorporate AI into your incident response procedures?
Addressing "Shadow AI": Clearly communicate policies regarding the use of unauthorized AI tools by employees. Offer approved alternatives and emphasize the potential risks of using unsanctioned AI.
Step 4: Monitor and Evaluate: The Continuous Improvement Cycle
AI is not a set-it-and-forget-it technology. It requires ongoing monitoring and evaluation to ensure it's performing as expected and delivering the desired results. This includes:
Regularly reviewing the performance of your AI systems and making adjustments as needed.
Staying informed about new AI technologies and threats.
Continuously educating your employees about AI and cybersecurity best practices.
Addressing Evolving Threats: As cyber threats evolve, so should your AI strategy. Regularly reassess your tools and tactics to stay ahead of the curve.
By embracing a continuous improvement mindset, you can ensure that your AI cybersecurity strategy remains effective in the face of ever-evolving threats.
Facts to consider:
According to Gartner, by 2025, 60% of organizations will use cybersecurity risk as a primary determinant in conducting third-party transactions and business engagements.
A Capgemini Research Institute study found that 69% of organizations believe they cannot respond to critical threats without AI.
The global AI in the cybersecurity market is projected to reach $46.3 billion by 2027, according to MarketsandMarkets.
In Conclusion: Embracing the Future of Cybersecurity with AI
In this ever-evolving digital landscape, AI is no longer a luxury, but a necessity for businesses seeking to thrive. It's a powerful ally that can amplify your cybersecurity efforts, detect threats with unprecedented speed and accuracy, and free your team to focus on strategic initiatives. But it's also a double-edged sword, with the potential for misuse and unintended consequences.
By following this practical guide, you can navigate the AI cybersecurity maze with confidence. Assess your needs, choose the right tools, develop a comprehensive strategy, and commit to continuous learning and improvement. Remember, AI is not a magic wand, but a powerful tool that, when wielded with intention, awareness, and mindfulness, can transform your approach to cybersecurity.
Key Takeaways:
AI is a Game-Changer: It's revolutionizing cybersecurity, offering faster threat detection, automated defenses, and improved decision-making.
The Risks Are Real: Be aware of the potential for AI-powered attacks, deepfakes, and ethical concerns.
Choose Wisely: Select AI tools that align with your specific needs and budget.
Develop a Strategy: A comprehensive AI cybersecurity strategy is essential for success.
Stay Vigilant: Monitor, evaluate, and adapt your approach as AI technology and threats evolve.
At Way2Protect®, we believe in empowering individuals and businesses to take charge of their cybersecurity and cyber safety. Our "Be I AM" principle (Be Intentional, Aware, and Mindful) is a powerful framework for navigating the digital world with confidence and peace of mind.
Are you ready to embrace the future of cybersecurity? Let's work together to create a world where we all live Happily Ever Cyber!
AI Cybersecurity FAQ: Your Burning Questions Answered
What exactly is AI in cybersecurity?
Think of AI as a digital detective and protector. It uses smart algorithms to spot patterns, detect threats, and respond faster than any human could. It's like having a 24/7 security team that never gets tired.
Isn't AI expensive? Can small businesses afford it?
While some advanced AI solutions can be costly, there are plenty of affordable options for businesses of all sizes. Think of it like choosing the right security system for your home—there's a solution for every budget.
Could AI actually make my company less secure?
AI can be a double-edged sword. In the wrong hands, it can create sophisticated attacks. But with the right approach and safeguards, it becomes your most powerful ally in the fight against cybercrime.
Do I need to be a tech expert to use AI for cybersecurity?
Not at all! Many AI cybersecurity tools are designed with user-friendliness in mind. Think of them as intuitive apps for your phone—you don't need to be a coder to use them effectively.
How can I choose the right AI cybersecurity tools for my business?
Start by assessing your specific needs and budget. Then, research different vendors and ask for demos or trials. Look for tools that are easy to use, scalable, and integrate with your existing systems.
What are the ethical implications of using AI in cybersecurity?
AI raises important ethical questions, such as potential bias in algorithms and privacy concerns. It's crucial to choose vendors who prioritize ethical AI development and to establish your own ethical guidelines for AI use within your organization.
How can I protect my business from AI-powered attacks like deepfakes?
Staying informed about the latest AI threats is key. Implement robust authentication measures, educate your employees about deepfakes, and invest in AI-powered tools that can detect and mitigate these threats.
Can AI replace my human cybersecurity team?
While AI can automate many tasks, it can't replace human expertise. Think of AI as a powerful tool that complements your team's skills, allowing them to focus on more strategic and complex issues.
Is my data safe with AI cybersecurity tools?
Choose reputable vendors with strong privacy policies. Understand how your data will be used and ensure that it's anonymized and protected.
What's the best way to get started with AI in cybersecurity?
Start with a small pilot project to test the waters. Partner with a trusted vendor who can guide you through the process and provide support. Remember, it's a journey, not a race.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



