Fortify Your Business with
Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
Fortify Your Business with Way2Protect's Ultimate Cybersecurity Shield
Transform cybersecurity from a challenge into your competitive advantage.
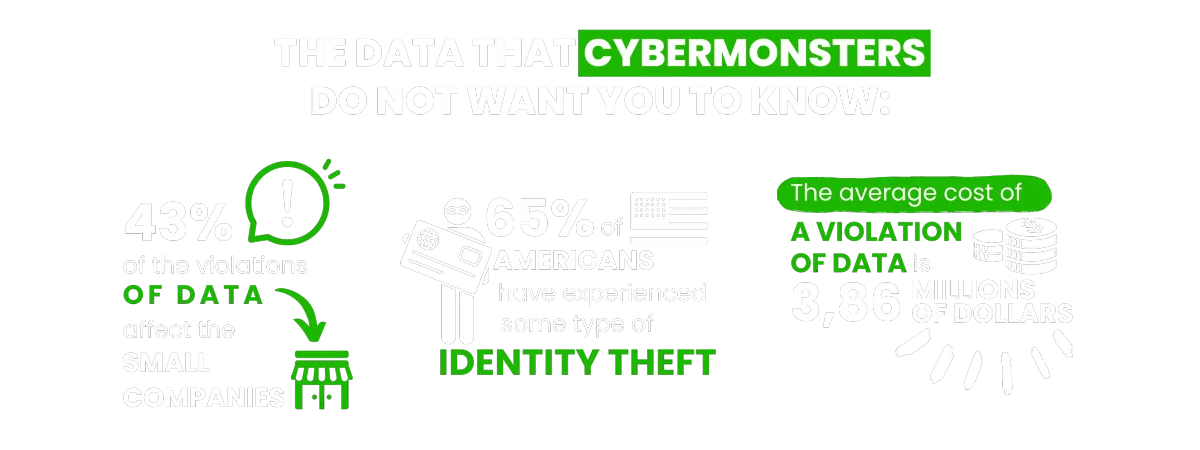
You find these and other figures in my book Happily Ever Cyber and on Cisa.gov

Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:


Find out how to push Cybermonsters away from your private data
With tips to help prevent a cyber attack protecting your family, work environment and yourself:
AS SEEN ON:

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Push Cybermonsters away from your private data.
Subscribe to my newsletter about cybersecurity and cyber safety. New issues every Tuesday.

Protect those that matters most to you:

Family
Protect your child(ren), teens,
and your parents.

Business Owners
Protect your data, your customer's information, your employees,
and your brand!

Yourself
Have peace of mind online!
International Bestselling & Award-Winning Cyber Safety Author
Identity theft & cyber crime can happen to anyone.




Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.
Why choosing us?
In a world full of digital distractions, we understand the importance of cultivating a healthy balance. At Way2Protect, our mission is clear: to be your trusted guide to a conscious and protected online experience, both for you and for what you value most: your family, your business, and your peace of mind.
Way2Protect becomes your fundamental ally in your digital world, providing you with hassle-free security and adapting cybersecurity practices to your routine without sacrificing your time. We facilitate the process, guiding you in the implementation of effective cybersecurity practices to protect your family, your business, and your work teams.

Get the latest news in the Cyber Security World

10 Essential Cybersecurity Tools Every Entrepreneur Needs in 2024
In today's interconnected world, entrepreneurs face an ever-growing array of digital threats. Protecting your business from cyberattacks is no longer optional—it's a necessity. This comprehensive guide will walk you through the ten most essential cybersecurity tools that every entrepreneur should have in their arsenal for 2024. From robust antivirus software to cutting-edge AI-powered solutions, we'll cover everything you need to create a formidable defense against digital threats.
Table of Contents:
Next-Generation Antivirus Software
Virtual Private Network (VPN)
Password Manager
Two-Factor Authentication (2FA) Solution
Firewall
Encryption Tools
Cloud Access Security Broker (CASB)
Security Information and Event Management (SIEM) System
Backup and Recovery Solution
AI-Powered Threat Detection and Response
1. Next-Generation Antivirus Software
Traditional antivirus software is no longer sufficient to protect against today's sophisticated malware and ransomware attacks. Next-generation antivirus (NGAV) solutions use advanced technologies like machine learning and behavior analysis to detect and prevent both known and unknown threats.
Key features to look for in NGAV software:
Real-time threat detection and prevention
Behavioral analysis to identify suspicious activities
Cloud-based threat intelligence
Automated remediation capabilities
Integration with other security tools
Story: The Tale of Sarah's Startup Sarah, the founder of a fast-growing tech startup, learned the hard way about the limitations of traditional antivirus software. One morning, she discovered her company's network had been infiltrated by ransomware, halting operations. After a costly recovery process, she implemented Crowdstrike Falcon, an NGAV solution, which detected and neutralized a similar threat within minutes. This proactive defense saved her company from a potential disaster, illustrating the vital role of NGAV in modern cybersecurity.
Popular NGAV options include Crowdstrike Falcon, SentinelOne, and Carbon Black.
2. Virtual Private Network (VPN)
A VPN is crucial for protecting your business data when accessing the internet from public Wi-Fi networks or working remotely. It encrypts your internet connection, making it nearly impossible for hackers to intercept your data.
Benefits of using a VPN:
Secure remote access to company resources
Protection against man-in-the-middle attacks
Anonymity and privacy when browsing online
Access to geo-restricted content
Improved overall network security
Story: Remote Work Woes When the pandemic forced many businesses to go remote, Carlos, an entrepreneur, realized the need for a VPN. Initially, his team used unsecured public Wi-Fi, leading to a data breach. After implementing NordVPN Teams, his company experienced a secure and smooth transition to remote work, highlighting the critical importance of VPNs in safeguarding business operations.
Recommended VPN services for businesses include NordVPN Teams, ExpressVPN, and Perimeter 81.
3. Password Manager
Weak or reused passwords are one of the most common vulnerabilities exploited by cybercriminals. A password manager helps create, store, and manage strong, unique passwords for all your accounts, significantly reducing the risk of unauthorized access.
Key features of a good password manager:
Strong password generation
Secure storage with end-to-end encryption
Cross-platform synchronization
Two-factor authentication support
Secure password sharing for teams
Story: The Password Predicament Lisa, a small business owner, used the same password for multiple accounts. A hacker exploited this, gaining access to sensitive information. Switching to LastPass, she generated unique passwords for each account and secured them with 2FA. This change not only enhanced her business security but also provided peace of mind.
Popular password managers for businesses include LastPass, 1Password, and Dashlane.

4. Two-Factor Authentication (2FA) Solution
Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of verification in addition to your password. This significantly reduces the risk of unauthorized access, even if a password is compromised.
Types of 2FA methods:
SMS or email codes
Authenticator apps (e.g., Google Authenticator, Authy)
Hardware tokens
Biometric authentication (e.g., fingerprint, facial recognition)
Story: The Extra Step that Saved the Day Mark, an e-commerce entrepreneur, implemented 2FA after hearing about increasing cyber threats. One day, he received a notification that someone tried to access his account. Thanks to 2FA, the attempt was blocked, demonstrating how an extra layer of security can thwart cybercriminals.
Consider implementing a 2FA solution like Duo Security, Okta, or Microsoft Authenticator for your business accounts and applications.
5. Firewall
A firewall acts as a barrier between your internal network and the internet, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. It's an essential component of any comprehensive cybersecurity strategy.
Types of firewalls:
Network firewalls
Host-based firewalls
Next-generation firewalls (NGFW)
Cloud firewalls
Story: The Invisible Shield Tom, running an online consulting firm, learned about firewalls after a minor cyber incident. Installing Fortinet FortiGate not only blocked future attempts but also gave him insights into potential threats, effectively acting as an invisible shield protecting his digital assets.
Popular firewall solutions for businesses include Fortinet FortiGate, Cisco ASA, and Palo Alto Networks.
6. Encryption Tools
Encryption is the process of converting data into a code to prevent unauthorized access. It's crucial for protecting sensitive information both in transit and at rest.
Areas where encryption should be implemented:
Email communication
File storage and sharing
Database protection
Mobile device security
Story: Secrets Secured When Maria, a freelance designer, accidentally sent a confidential file to the wrong client, she realized the need for encryption. Switching to ProtonMail for secure emails and VeraCrypt for file encryption, she ensured her communications and files were protected, preventing future mishaps.
Consider using encryption tools like VeraCrypt for file encryption, ProtonMail for secure email, or full-disk encryption solutions like BitLocker for Windows or FileVault for macOS.
7. Cloud Access Security Broker (CASB)
As businesses increasingly rely on cloud services, a CASB becomes essential for maintaining visibility and control over data stored in the cloud. It acts as a security policy enforcement point between cloud service consumers and providers.
Key capabilities of a CASB:
Visibility into cloud usage and shadow IT
Data security and loss prevention
Threat protection
Compliance monitoring
Access control and user authentication
Story: The Cloud Conundrum Jorge, who runs a tech startup, faced challenges securing cloud data. Implementing Netskope CASB allowed him to monitor cloud usage, enforce security policies, and protect sensitive data, providing a comprehensive solution to his cloud security needs.
Leading CASB solutions include Microsoft Cloud App Security, Netskope, and Symantec CloudSOC.
8. Security Information and Event Management (SIEM) System
A SIEM system collects and analyzes log data from various sources across your IT infrastructure to provide real-time monitoring, threat detection, and incident response capabilities.
Benefits of implementing a SIEM:
Centralized log management and analysis
Real-time threat detection and alerting
Automated incident response
Compliance reporting
Forensic analysis capabilities
Story: The Eye in the Sky When a breach occurred at Rachel’s marketing firm, their SIEM system, Splunk, quickly identified the anomaly, allowing her team to respond immediately and mitigate the damage. This experience underscored the importance of having a vigilant SIEM system in place.
Popular SIEM solutions include Splunk, IBM QRadar, and LogRhythm.
9. Backup and Recovery Solution
Regular backups are crucial for protecting your business data against loss due to hardware failure, human error, or cyberattacks like ransomware. A robust backup and recovery solution ensures that you can quickly restore your systems and data in case of an incident.
Key features to look for in a backup solution:
Automated, scheduled backups
Incremental and differential backup options
Cloud and on-premises storage options
End-to-end encryption
Quick and easy recovery process
Story: The Last Line of Defense Emma, a boutique owner, experienced a ransomware attack that encrypted her entire inventory database. Thanks to regular backups with Acronis, she restored her data within hours, minimizing downtime and loss, highlighting the critical role of a reliable backup solution.
Consider solutions like Veeam, Acronis, or Carbonite for your business backup needs.
10. AI-Powered Threat Detection and Response
Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing cybersecurity by enabling faster and more accurate threat detection and response. These technologies can analyze vast amounts of data to identify patterns and anomalies that might indicate a security breach.
Benefits of AI-powered cybersecurity tools:
Proactive threat hunting
Reduced false positives
Faster incident response times
Continuous learning and adaptation to new threats
Enhanced network visibility
Story: The Smart Defense Alex, an app developer, adopted Darktrace’s AI-powered cybersecurity tool. One evening, the system flagged an unusual data transfer. The AI’s quick detection and response prevented a data breach, showcasing how AI can be a game-changer in protecting digital assets.
Leading AI-powered cybersecurity solutions include Darktrace, Cylance, and IBM Watson for Cyber Security.

Conclusion
As an entrepreneur, protecting your business from cyber threats is paramount. By implementing these ten essential cybersecurity tools, you'll significantly enhance your company's security posture and reduce the risk of falling victim to a cyberattack.
Action Steps:
Assess Current Security Measures: Evaluate your existing security tools and identify gaps.
Prioritize Implementation: Based on your specific needs and risk profile, prioritize which tools to implement first.
Regular Reviews: Continually review and update your security measures.
Employee Training: Ensure your team is educated on cybersecurity best practices.
Stay Informed: Keep up with emerging threats and new technologies.
By taking these steps, you can safeguard your business's future, allowing you to focus on growth and innovation with the confidence that your digital assets are protected.
Live Happily Ever Cyber!

Sandra Estok
Subscribe for more ways to protect what matters most to you against hackers, scammers, and Cybermonsters™



